Blog
Blog post list
The History of Hacking: From the 19th century to today
The threat of hacking is a major problem for today’s interconnected world, but its history is a little less settled....
Mar 9, 2022, 11:10:44 AM
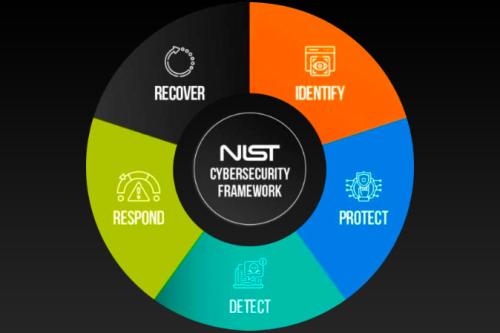
A quick introduction to NIST Cybersecurity Framework
NIST Cybersecurity Framework, published by the United States National Institute of Standards and Technology,...
Jan 21, 2022, 12:18:45 PM

On the wisdom of getting a pen-test
With cost being a top-of-mind concern for small and medium sized enterprises, cybersecurity in general......
Dec 21, 2021, 2:40:49 PM

Colonial Pipeline Cyber Attack: Lessons Learned
Ransomware attack on Colonial Pipeline caused a significant disruption and here are major lessons......
Dec 10, 2021, 12:58:19 PM

Ransomware Resilience Strategies
An organisation is hit with a ransomware attack every 11 seconds and the bad actors are getting smarter....
Dec 6, 2021, 2:07:41 PM

Don’t become an unknowing member of a botnet!
Releasing malware into poorly defended networks has been a key method of choice for malicious actors....
Nov 29, 2021, 3:23:21 PM

Cyber Resilience
Cyber resilience is the ability of an organisation to operate its business and accomplish objectives, regardless of any adversaries....
Nov 23, 2021, 5:18:01 PM

Go for Zero Trust!
In a world where cybersecurity threats are abundant, multiple layers of security are often required to provide maximum assurance....
Nov 17, 2021, 10:13:10 AM

Audit Vs. Assessment
A cybersecurity audit is a point-in-time evaluation while an assessment is a high-level analysis of cybersecurity controls....
Nov 9, 2021, 11:08:47 AM
